*It should be noted that I’m by no means an expert. This exercise is largely in the interest of validating understanding, and confirming some research and topics, as well as answering a question I was asked recently. I welcome feedback, discussion, and criticism of any of the points below via any channel!
Botnets are one o
What is a Botnet?
A botnet is quite simply a robotic network designed to receive some sort of command or direction. At the risk of dating the author, you might recall the Apple 1984 Super Bowl Commercial with a decidedly Orwellian feel wherein a group of individuals stares at a screen shouting direction and de-motivation in order to desensitize.

The Matrix analogies were too plentiful and easy, and I couldn’t make a “Where’s the Beef” reference fit. Photo by Markus Spiske on Unsplash
In this example, the botnet is the folks in the chairs accepting what’s put in front of them. The botnet is essentially a wide array of computers or other internet-connected devices which have been infected in one way or another and are now under the control of the botnet commander, owner, h@ckm0nst3r or whatever moniker they adopt. At this point, the face on the screen in the example is the point of command and control – the point from which the malicious attacker manages the bots. The folks in those seats are sitting, infected, waiting for their next command. Botnets have also matured greatly over the years, evolving the ability of their somewhat simple nature to control malware via Instagram, Github, and more. The natural question is how then, do the seats for our botnets get filled in? While there are numerous means of infection/compromise, too many in fact to cover here and now, some common techniques include drive-by compromise, and spearphishing via link or attachment (see; targeted fraudulent and malicious messages crafted for the specific purpose to have the target click something initiating either a download or redirection in the aim of credential harvesting for additional endpoint/network compromise).
The Purpose and Goal of a Botnet
Typically, when an actor sets up a botnet, the goal is going to be to cast the widest net possible and stay on systems, undetected as long as possible. A wider net means more compromised systems, more compromised systems mean more distributed computing power, and more distributed computing power means better chances at accomplishing your goal. Now then, what is the goal? The goals for a botnet are varied and widespread, typically, but not exclusively tying back to two main aims: availability/disruption & financial gain. Sometimes it can be both, and often one will affect the other.

Botnets can disrupt an entire network, distributing ransomware, flooding network equipment with so much traffic that it panics and locks up, or in the case of the infamous Mirai botnet, scanning the Internet of Things (IoT) space and using a table of more than 60 default username and passwords to log in and infect those devices, add to the botnet, and continue the scanning cycle. At the risk of a slight tangent, one important lesson from Mirai is anything you purchase – be it personally or professionally that hooks to the web, needs its default credentials reset immediately – if you cannot locate how to do this or there is a remote possibility of hard-coded credentials in your equipment, buy new equipment. Botnets are tools used to serve a purpose – without something sending the commands the botnet itself is useless. If a botnet were a shiny new Power Wheel you got on a day late in December, it’d be a great piece of plastic – however, without the batteries to give the wheels commands to tear around the driveway, all you have is a great piece of plastic. Botnets are connected to command and control (C&C) servers to receive direction. These instructions will vary based on motivation and purpose, but typically relate to the previously laid out cases: lay low and wait for a signal to attack, scan/infect more and add to the horde, start siphoning that sweet CPU, start sending out social media/email en masse to confuse and muddy what “truth” is online, or much more.

While the purpose of a botnet is based on motivation, the risk of a botnet to an organization is substantial. We’re talking about your endpoints being compromised and utilized for another purpose completely unrelated to your business making money or serving your customers be it for or non-profit. The saying you don’t know what you don’t know seems obvious, but applicable here especially. If you’re not apprised of what your endpoints are doing, who they’re reaching out to, and what the content of those connections are, you’re flying both without your targeting computer and the Force is not on your side.
“There is no try [with a botnet]…do what is commanded you will.”
InfoSec Yoda, a totally real Muppet.
Botnet Design
In the most reductive way possible, let me illustrate essentially how we would throw something together in order to build a botnet. Below is an admittedly rough outline of a botnet – not very sophisticated, but that’s also the most reductive kind of description for a botnet – a network of computers that awaits commands from a server (nearly every network/server/client relationship can be described this way).
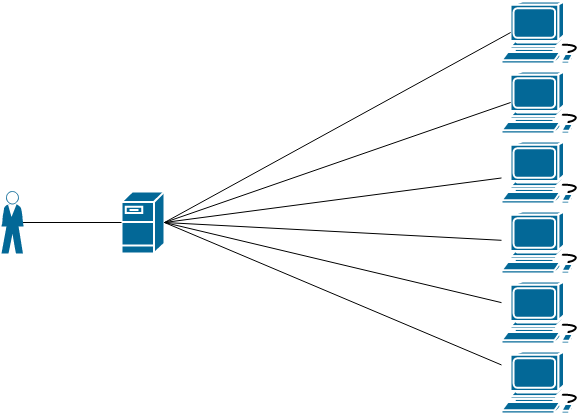
So, we know what we have as a general idea of the workflow – first we need a Command and Control server up top to dictate the “what” of our messages. If we’re designing said botnet (do not recommend, do not do unless you can unequivocally state you have a properly walled-off sandbox/virtual farm!!), we’d also either develop or purchase (yes, literal marketplaces exist) malware or a payload that would help us get our sneaky software onto endpoints. These days there’s a huge influx in fileless malware, so we might find a payload that is a word doc, which launches PowerShell, which then invokes expressions from encrypted Base64 strings, pulling down a second payload containing the real sledgehammer malware. For the sake of discussion and the illustration above we want our botnet to establish connections and maintain a peer-to-peer connection across all the devices it touches, ideally keeping the botnet on devices longer and making it tougher to track down. So once the initial malware hits the system, it kicks off a process pulling down other pieces of the puzzle – however we can also add a timer, keeping this next, more intrusive step under the radar for an amount of time we specify. The possibilities here are near endless – and for defenders, terrifying. In summary the botnet we just configured basically does the following;
- Infection/Establish Connection – my choice of infiltration was fileless malware that uses PowerShell and C# which is already built in to the Operating System and avoids writing directly to the hard drive. Some organizations and especially real-world users wouldn’t even know what to look for here.
- Calls home to the C&C server – a very low bit size “ping” of sorts to let us know that the bot is in the net, and that the C&C server sees it. From here we branch to a few tactics depending our end goal and what we want to accomplish quickly.
- Snoop – check out what other devices are out there – how many Windows devices are we looking at and what versions? How about servers? Are there multiple sites? Can I see any security artifacts? What are we dealing with? Typically, this is where risk of spotting or red flags becomes higher – as our script or server starts poking around, inevitably we start to leave breadcrumbs.
- Spread – Establishing peer-to-peer connections to other machines and attempting to spread the infection (casting an even wider net) allows us to add to the net increasing our reach, compute power, network capabilities, and much more. Since the goal of a botnet is to “be big”, this tactic is valuable in widening the scope and impact. There’s a fun formula used in communications and Project Management that says for N points of contact there are n(n-1)/2 lines of communication. This means for N there are x amounts of network connections and potential points of contact for an endpoint. Think about it – if you have 10 machines networked in a peer-to-peer fashion, you’ve got 45 total lines of communication. 45 potential points of reinfection. While this isn’t cemented in theory within the re-transmission/infection of a botnet, it’s an interesting theory to explore.
- Download – if you want to get caught quickly and cause some damage as soon as you can – download and execute is a good way to do it. If an organization or individual isn’t watching or monitoring their logs and network ingestion, they might not notice much more than network slowdown. In some of these scary scenarios where there is no network anomaly detection, log review, IDS/IPS, or SIEM in place the network slowness would build frustration, IT would get tickets, and eventually a network engineer would have a “going to need a bigger boat” moment. Downloading can also be done in a low and slow method – and I’ll loop in data exfiltration here – because we could also very slowly let data start flowing out the window like the good smell lines on a pie in Looney Tunes. These activities, if you’re on the Blue Team are what you really hope to not see – because it might become a case of tracking down what is gone, if it’s IP, and if the company is going to make it based on scope and impact.
- Lay Low – the last option is to get on and hang on. We don’t necessarily have to kick anything off, and if no one knows we’re here, we can sit on this compute and network gold until we need it and fire off a signal in the future to take down our target. Have a vendetta? DDoS for hire is a thing – and we’ve just essentially loaded the gun.

Symptoms of Botnet Infection
Do you have a user who has been complaining that ever since January their computer is deathly slow, on its last leg, or files are taking a long time to open? Is there some slightly strange network traffic outgoing to an address that starts at a definitive time but doesn’t look familiar? Is there outgoing traffic on a protocol that it shouldn’t be? Basically – is there something weird…in your neighborhood? (It had to be done). If you’re not sure, first things first – if it’s a corporate asset – call or email your internal team for a quick diagnosis! IT Teams would much rather have to run a scan and take a good look than have no clue – also IT Teams note and create tickets for each of these instances, so this is a great way to create an audit trail in case something does seem off in the future. If you want to do a bit of self-diagnosis, here are a few quick things to check;
- Task Manager – (Windows 10) Right-click the taskbar (or Windows button in the lower left) and select Task Manager. From the Processes tab, click “Network” to sort by network activity – anything unfamiliar and high up that list should be investigated
- Task Manager – Disk Usage – Same process as above – this number might be fluctuating as different “stuff” on your machine runs and accesses the disk, however, if something is consistently near the top and completely unfamiliar or seemingly randomly named (random letters, uppercase/lowercase) then it should be looked at.
The symptoms of a botnet are varied – however, it’s important to note that we cannot simply rely on endpoints like laptops, desktops, and workstations to be infected. As covered earlier, Mirai, a frankly sleep-preventing botnet in the wild infects IoT devices en masse and with an admirable scope. This is reiterated here because it can’t be said enough – when you purchase a new device, change whatever password came on it. A topic for another article but very important is that you should document this in a Multifactor Authentication-backed Password Vault (LastPass, Dashlane, KeyPass, etc.).
But what now?
If you find signs that your computer might indeed be a walking dead extra soon, contact IT immediately and try to document as much as possible. For system administrators and IT teams, test your backups regularly because one of the only sure-fire ways to recover is to factory reset/wipe the device. You can attempt to run a virus scan or use another tool to check for rootkits or bootloaders, but in all reality incident response is an entire discipline and specialty that is best left to the pros. Be very careful (i.e. do not) connecting removable media to any device that may be compromised, investigate network traffic and communication and be sure to notate everything found as you work through your process.
A question typically arises as to prevention – and while there are a few tools of the trade like network anomaly detection, fileless malware detection and response (sometimes called anti-evasion software), traditional signature-based antivirus, and endpoint detection which are vital in the detection and response game, prevention is an entirely different beast in that it truly comes down to one thing: user education and training. If you’re a system administrator and are concerned about potential botnet activity, ransomware, data exfiltration, or other malicious behavior the best possible thing that can be done early and often is user education. Everyone regardless of professional or personal setting should be familiar with scam and spam emails, making these educational and informative for users is vital – all the while not feeding the Fear Uncertainty and Doubt monster. Information is power in the hands of the user, utilizing tools to illustrate the size and scope of data breaches, the importance of password hygiene, and the crucial moments from opening an email to step 2 are imperative for every single user to understand. We like to say the bad guys only need you to mess up one or two times, where they get to fail consistently all day long. Send out regular email updates, sign up for a Security Testing and Training service, hold annual/biannual/quarterly awareness trainings that are engaging while informational (sometimes much easier said than done).
The bottom line across most malware and infection-related articles, news items, and information is that education is key – for administrators, you need to be apprised of all the latest threats, risks, and vulnerabilities in your environment. For users, you need to know how to spot the “bad” and get information to the right people so they can respond quickly. Malware and malicious actors are not resting, nor are they happy with how things currently work – as the defenders, we must all remain vigilant and talkative, and as the industry progresses the freedom and responsible reaction to events becomes even more important.









